Courses
- Web Development
- Data Analytics
- Data Science with AI
- Cyber Security
- Python
- Django
- C Language
- C++
- Java Training
- Data Structure
- Algorithm
- Front-end Development
- JavaScript, jQuery & Ajax
- React.js
- Node.js & Express.js
- MySQL
- SQL
- PL/SQL
- Oracle
- MongoDb
- SQLITE
- ADCAT
- ADCA
- DCA
- Tally Prime
- Advance Excel
- COA
- ADOA
- GST
- TAT
- TDS & Payroll

Cyber Security
Has your social media handles or phone ever been hacked? Why compromise with your
personal data when you can secure it on your own?
In the era of 'Everything on Internet' data security has become the basic requirement of our day to
day life. From ATM pins to personal photographs everything has to be protected by any means. You must
have heard about data leakage from government database. Also, recently there was a huge data leakage
from Facebook, Yahoo! and many other platforms. Ever thought how is this even possible? Have you ever
wondered how do the companies secure their information, who are those who help companies secure such
data?
If you are looking for an answer, you are at the correct place. Yes, you heard it right. We at Rays
provide you with a complete course on Cyber Security.
Cyber Security is one of the most trending and has become a need for every one.
| Course Name | Date & Time | Batch Code | Take Demos |
|---|---|---|---|
| Offer Batch Python | 27/11/2023 | pob2a9qx | View Details |
| Core JAVA(J2SE) | 11/12/2023 | repljava211 | View Details |
| C Language | 11/12/2023 | clob289i4 | View Details |
| DS(Data Structure) | 11/12/2023 | replds111 | View Details |
Why Cyber Security?
- Emerging Sector: In this ever competitive world, phishing and data theft has become the most common problem so in order to secure the sensitive data and information the job of a Cyber Security Expert becomes very crucial and is demanded the most.
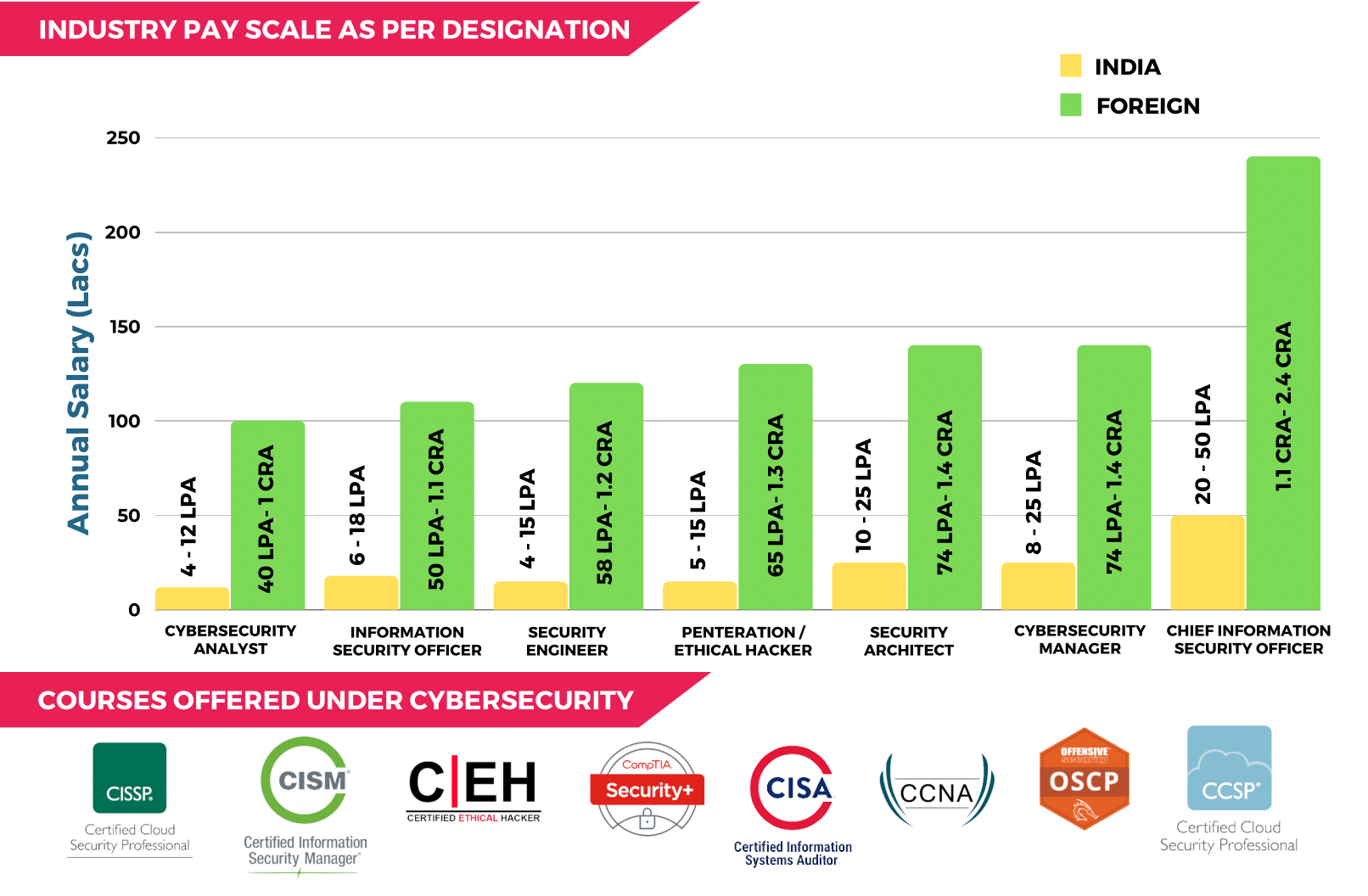
- Great Salary Prospects: Cyber Security Experts are one of the most highly paid jobs in the industry. As a beginner, one can earn around 5 lakhs to 25 lakhs per annum in India.
- Compulsory Complainces: All the companies across the world use huge data to work upon. Protection of that data has become a compulsion, government has laid various norms which makes it compulsory for companies to hire Cyber Security Experts so the role of these experts are at a huge demand.
WHY REPL?
- Life time validity (enroll one time and revise many times)
- Interaction with the best faculty and Industry Experts
- Small Batches to focus on each student
- We focus on both theoretical and practical approaches in a parallel way.
- You will be given the opportunity to work on a live project.
- Outdoor activities to boost your confidence.
- Presentation in class by the students.
Our Key Features:
- Good Quality Material Notes
- Smart Classes Available
- Online Test
- Chapter wise Assignments
- Offline And Online Classes
- Recorded class on Rays App
- Eminent faculties of the IT Industry( Amazon, Wal-Mart, Oracle, Microsoft..)
- Fully AC and Wi-Fi Campus.
Syllabus
Cyber Security & Ethical Hacking
- What is Cyber Security & Ethical Hacking?
- Difference between Hackers (White Hat, Black Hat, Grey Hat)
- Types of Cyber Threats: Malware, Phishing, Ransomware, etc.
- Cyber Law, Legal Aspects, and Compliance (Indian IT Act basics)
- Cybersecurity Domains: Network Security, AppSec, SOC, Cloud, IAM
- CIA Triad: Confidentiality, Integrity, Availability
- Creating VM lab using VirtualBox
- Installing Kali Linux & Windows 10 VM
- Exploring the Cyber Kill Chain and MITRE ATT&CK
- Understand cybersecurity career paths
- Hands-on Linux setup and terminal usage
- OSI & TCP/IP Model
- Subnetting, IP Classes, IPv4 vs IPv6
- Devices: Switch, Router, Firewall, IDS/IPS
- Protocols: TCP, UDP, HTTP, DNS, DHCP, ARP
- Basic Linux Commands
- File System Hierarchy & Permissions
- Shell Scripting (Intro to automation)
- Networking Lab with Packet Tracer or GNS3
- Shell scripts to automate file creation, backups
- Configuring static and DHCP IPs in Linux
- Basic networking skills with Linux automation experience
- Windows Architecture & Security Components
- Password Cracking Techniques (Offline & Online)
- Tools: John the Ripper, Hydra, Medusa
- Privilege Escalation Basics (Windows/Linux)
- Understanding SAM, BIOS, Registry
- Keyloggers, Trojans, and System Backdoors
- Cracking local user accounts in a Windows VM
- Creating custom payloads using msfvenom
- System hardening practices
- Hands-on password attacks and defense understanding
- Web App Architecture (HTTP, Cookies, Sessions)
- Introduction to OWASP Top 10
1.) SQL Injection, XSS, CSRF 2.) File Inclusion (LFI/RFI) 3.) Command Injection 4.) Insecure Deserialization - Setting up DVWA, BWAPP, JuiceShop
- Introduction to Burp Suite (Manual Testing + Automation)
- Reporting & Documentation Format
- Vulnerability exploitation in DVWA
- Automated scans using Nikto, OWASP ZAP
- Custom reports with findings and mitigations
- Proficiency in discovering and reporting real web bugs
- Wireless Protocols: WEP, WPA, WPA2, WPA3
- WiFi Cracking: Handshake Capture & Cracking
- Aircrack-ng Suite: airmon-ng, airodump-ng, aireplay-ng
- Cryptography Basics: AES, RSA, Hashing
- Steganography Tools (Steghide, OpenStego)
- Google Dorking
- OSINT Tools: Shodan, theHarvester, Maltego (Intro)
- Capturing WiFi handshakes & cracking passwords
- Hiding messages in images using steganography
- Finding vulnerabilities using Google Dorks & Shodan
- Perform real WiFi attacks & open-source investigations
- Introduction to Vulnerability Assessment vs. Penetration Testing
- Tools: Nmap, Nessus, OpenVAS
- Report writing & project documentation
- Interview Preparation: Resume, Mock Interviews, Role-Play
- Career Guidance & Freelancing Tips
- Google Dorking
- OSINT Tools: Shodan, theHarvester, Maltego (Intro)
- Vulnerability Assessment of a Web Application
- WiFi Cracking & Hardening Report
- Full Red-Teaming Simulation on Local VMs
- Bug Bounty Practice on platforms like PortSwigger Labs or TryHackMe
- Industry-ready skillset with portfolio project and CV
Recent Posts

Chatbot
-
Hi there
How can I help you today?

Request A Demo!
|
|
|
|
|
|
|
|
